Security is hard to understand, difficult to implement and just plain gets in the way of progress. If you are thinking that it is something you can leave until later, think again.
In this post I provide an overview of some of the security aspects that you need to consider.
Caging the Elephant
There is a saying…
‘How do you eat an elephant? … One bite at a time.’
It is good advice, tackling small chunks at a time allows you to see progress and to adapt quickly without getting bogged down in large, complex problems.
There is another angle though…
‘How do you cage an elephant?’
When caging an elephant, putting up single bars at a time will not be very effective. The elephant will smash the flimsy cage and escape. So, how do you cage an elephant? You must first build the entire cage, build it strongly and then put the elephant in it.
And so it is with security. You cannot build just part of your security because security is only as strong as its weakest link and by restricting your security design you will soon be facing a breach. You may not even know about it until an angry customer comes to you with claims their data has been illegally accessed.
Security breaches can destroy your business overnight.
Security Considerations
There are several different aspects to security. Not all might apply to your product but it is certain that at least one will.
- Prevent unauthorised access to your customers’ data
- Prevent unauthorised modification to your customers’ data (including deletion)
- Prevent unexpected loss of your customers’ data
You may think that the data you hold is not sensitive or valuable. Most jurisdictions around the world may disagree. Whether it is the Australian Privacy Principles (APP), the European General Data Protection Regulation (GDPR) or the US Health Insurance Portability and Accountability Act (HIPAA), you will find that the data you collect from your customers belongs to them and that they have the right to expect you to secure it and ensure it is only used for the agreed purposes.
The implications of not securing this data can significant.
Security is a serious business.
Building a Solid Security Foundation
Security is one part of your architecture that needs to be well thought out before you start building. By designing the security early on, it ensures that it is considered during the build of every feature and function and not left until later. Retrofitting security is rarely a good approach and can mean extensive rebuilds of your product, if you are still in business.
The thing is, security is hard to get right. Few of us think like a cybercriminal does and this makes us blind to the weaknesses in our product. You do not see the attack surfaces and attack vectors that allow an assailant to gain unauthorised access to your system. Your product works and you and your customers are delighted, what more do you need?
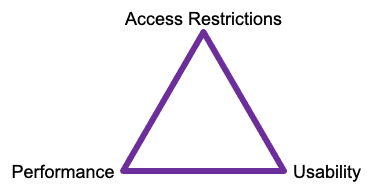
The Security Triangle
When talking about security it is important to remember the security triangle:
Copyright 2020 Requillion Solutions
Imagine your front door. It can be made secure by making it out of steel and welding it shut. Not very usable.
Alternatively, you can leave it wide open. Very useable but not very good at stopping criminals.
Or you can opt for a system of 6 different locks to secure the door. Yep, its secure. Yep, you can still get in. But boy, does it take time to get into your house.
Security is always a compromise between accessibility, usability and performance. Because it is a compromise, there will always be a criminal element willing to get their hands on the information you hold. Your job is to make it harder than the next product so they go there instead.

Photo by Wilhelm Gunkel on Unsplash
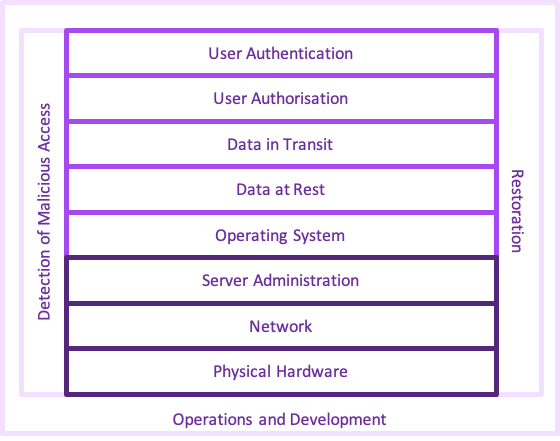
Layered Security
Security is like Ogres, or, if you are not familiar with Shrek, like onions. It has layers.
Each layer is designed to prevent unauthorised, malicious or accidental modification or access to information. As security is only as strong as its weakest layer, it is important to address all the layers.
The set of layers you need to consider are shown below.
Copyright 2020 Requillion Solutions
Each of these is a blog in its own right, so I will focus on the basics.
From this diagram, you may be starting to understand why security is often left until last.
Security of the Cloud
The ability to quickly and cheaply spin up new servers makes it easy to decide to put your product into the cloud. However, placing your product in the cloud will not ensure it is secure.
I like the way Amazon Web Services (AWS) talks about their security. They talk about ‘security of the cloud’ versus ‘security in the cloud’. It is a subtle difference but a very important one.
AWS and other cloud providers will secure the physical servers, the network, the connectivity and to some extent, the system administration. This is security of the cloud and addresses the first 3 layers. Whilst these layers are important, it does not make your application secure.
Security in the Cloud
You must secure the remaining layers to achieve security in the cloud. These are described below.
Operating System
Ensure that you use the latest OS and that it is always up to date and appropriately secured, including users, file systems, system processes, ports, digital certificates and passwords.
Securing the Data at Rest
Remember that whilst you always intend for people to access your product through your application, this may not always be the case. Attackers may gain access to your database or filesystems. They may even steal your disk drives. This layer is securing Data at Rest.

Photo by David Clode on Unsplash
Here are some of the common areas that are overlooked during development of a product:
- Filesystems – encrypt and restrict access to specified users
- Proxies and gateways – be aware of caching and buffering
- Databases – encrypt where possible or at least secure the filesystem
- Logs – do not log sensitive data
- Data sovereignty – abide by regional restrictions when selecting cloud providers
Securing the Data in Transit
Users of your product create and consume information. That information is transferred from their application (be it a mobile application, browser etc) to your servers. This is referred to as Data in Transit.

Photo by Mado El Khouly on Unsplash
Consider this information to be gold. It is highly sought after and very valuable. You do not want someone stealing it as it is transferred to the bank.
Thankfully there are ways to protect the connection between your application and the server using encryption protocols, eg: TLS and HTTPS. However, this is an evolving technology and vulnerabilities are regularly being uncovered, leading to new standards being developed. It is important not to just use encryption but to use the right encryption methods.
All connections, even between your processes, should be secured through encryption.
Notifications are a potential gold mine for thieves. Avoid placing any sensitive information in notifications such as emails, text messages and push notifications. Rely on the security of your platform. Be aware that intercepted notifications can be changed and this can lead to credentials being stolen.
User Authorisation
Your product must determine whether the user is authorised to access the information and features being requested.
How your product makes this determination depends on the access controls you need. Options include:
- Role Based Access Control (RBAC) – access granted to all people with a given role
- Attribute Based Access Control (ABAC) – access granted based on the data itself
- Context Based Access Control (CBAC) – access granted based on the context of the request
User Authentication
Authentication is the process by which you work out who the user is. There are different ways in which this can be done, from the simple username/password, through two factor authentication and digital certificates to passwordless access.
Your database of users is as important to secure as any other information you have. One attack surface is to obtain user credentials so that you can impersonate an authorised user.
Detection of Malicious Access
No system is 100% secure. It is just a matter of time before it is breached. This is where detection comes in.
There are systems that you can deploy to monitor user traffic and detect abnormal patterns of behaviours. These systems are becoming increasingly sophisticated.
Remember, there are regulatory requirements on reporting security breaches.
Restoration
Following a breach, data may be lost or modified. It is important to be able to restore your system from your backups. Some ransomware attacks not only target your local and networked drives but also your back up media.
Whether you rely on your backups in case of system failure or because of cyberattacks, it is important to regularly test your backups and your restoration processes. Like any insurance policy, you hope to never have to use it but want it to be there when you do.
Operations and Development
Operations and development can easily be forgotten but it is an important part of today’s security. Depending on your product, you may need to consider security around aspects such as:
- Who does the development and where
- Where the code is being held
- The libraries being used
- The build to deployment pipeline
- The location and contractual commitments of the operational staff
- The location and sovereignty of the data
- User credentials for all staff
- Operational processes and practices
- Breach processes, including notification and recovery
Specialist Advice
Ultimately your business will be impacted if you have a breach in security, but you may not be the only victim as your customers may also suffer from the breach.
Rather than taking a chance on compliance and security, you should engage an expert security consultancy to review your designs and implementation to determine if they are suitable for the use they are intended for. Whilst this can be expensive, it will provide peace of mind for you and your customers.

Photo by Liam Tucker on Unsplash
Conclusion
Security can seem complex and difficult, and it is. This should not be the reason to ignore it. Weaknesses in your security framework can lead to the rapid collapse of your business, even from day one.
Remember:
- Build security in from the very start.
- Select an appropriate, layered security model.
- Use pre-defined architectures and libraries.
- Test, test and test.
- And then get your product tested formally.
And do not forget that security is not set and forget. It must be constantly monitored, tested and updated.
This blog has hardly scratched the surface. At Requillion Solutions, security is always at the top of our minds when we are proposing solutions. It forms a central theme of our reference architecture and our solution developments. If you would like to learn more, please contact us.
And if you were wondering, putting a model Storm Trooper in front of your system and hoping that it will frighten off the cybercriminals is not an appropriate strategy!